VPN with MFA «passwordless»
See also this project: https://github.com/matteocorti/vpn_eth
In both cases (macOS or Linux), extend your PATH as follow:
[ ! -d ~/bin ] && mkdir ~/bin
export PATH="${HOME}/bin:${PATH}"and also add the export command in you shell configuration (ex. ~/.zsh, ~/.bash_profile, ~/.bashrc).
Setup for macOS with Cisco Secure Client
Step 1
Install the oathtool tool, needed to generate the OTP code from command line:
# with MacPorts
sudo port install oath-toolkit
# with Homebrew (not yet tested)
brew install oath-toolkit
# from Source
curl -s -L -O https://download.savannah.nongnu.org/releases/oath-toolkit/oath-toolkit-2.6.11.tar.gz
tar xf oath-toolkit-2.6.11.tar.gz
cd oath-toolkit-2.6.11
./configure
make
cp -a oathtool/{oathtool,.libs} ~/binStep 2
Save your VPN Password to your Keychain Access as follow:
U="your_username"
security add-generic-password -a $U -s ethvpn -l "ETH VPN password for $U" -U -w
==> Enter your ETH WiFi/VPN passwordStep 3
Save your OTP Secret (see below About the «OTP Secret») to your Keychain Access as follow:
U="your_username"
security add-generic-password -a $U -s ethotp -l "ETH OTP secret for $U" -U -w
==> Enter your ETH OTP secretStep 4
Create a script called vpn in your ~/bin like this:
#! /bin/bash
USER="your_username"; # <--- change this with your ETH username
VPN_SERVER="sslvpn.ethz.ch";
VPZ_NAME="math-guest";
REALM="math-guest";
VPN_PASSWORD="$(security find-generic-password -a $USER -s ethvpn -w)";
OTP_SECRET="$(security find-generic-password -a $USER -s ethotp -w)";
OTP_CODE="$(oathtool --totp=sha1 --time-step-size=30 -b "${OTP_SECRET}")";
VPN="/opt/cisco/secureclient/bin/vpn"
case $1 in
c)
if ${VPN} -s status | grep -q Disconnected; then
echo -e "${USER}@${REALM}.ethz.ch\n${VPN_PASSWORD}\n${OTP_CODE}\n" | ${VPN} -s connect https://${VPN_SERVER}/${VPZ_NAME};
open -a "Cisco Secure Client";
else
echo "=> already connected";
fi;;
d)
if ${VPN} status | grep -q Connected; then
${VPN} disconnect;
else
echo "=> already disconnected from";
fi;;
i)
${VPN} status;;
*)
echo;
echo " Usage: <c|d|i>";
echo " c : connect";
echo " d : disconnect";
echo " i : info";
echo;
exit;
esac;and set the correct permissions:
chmod 700 ~/bin/vpnSetup for Linux with OpenConnect
I'm working on it...
Usage
Start VPN:
vpn cStop VPN:
vpn dCheck if VPN is running or not:
vpn iAbout the «OTP Secret»
You get your OTP Secret when you register the first time for MFA (Multi-Factor-Authentication) as shown in the following screenshot:
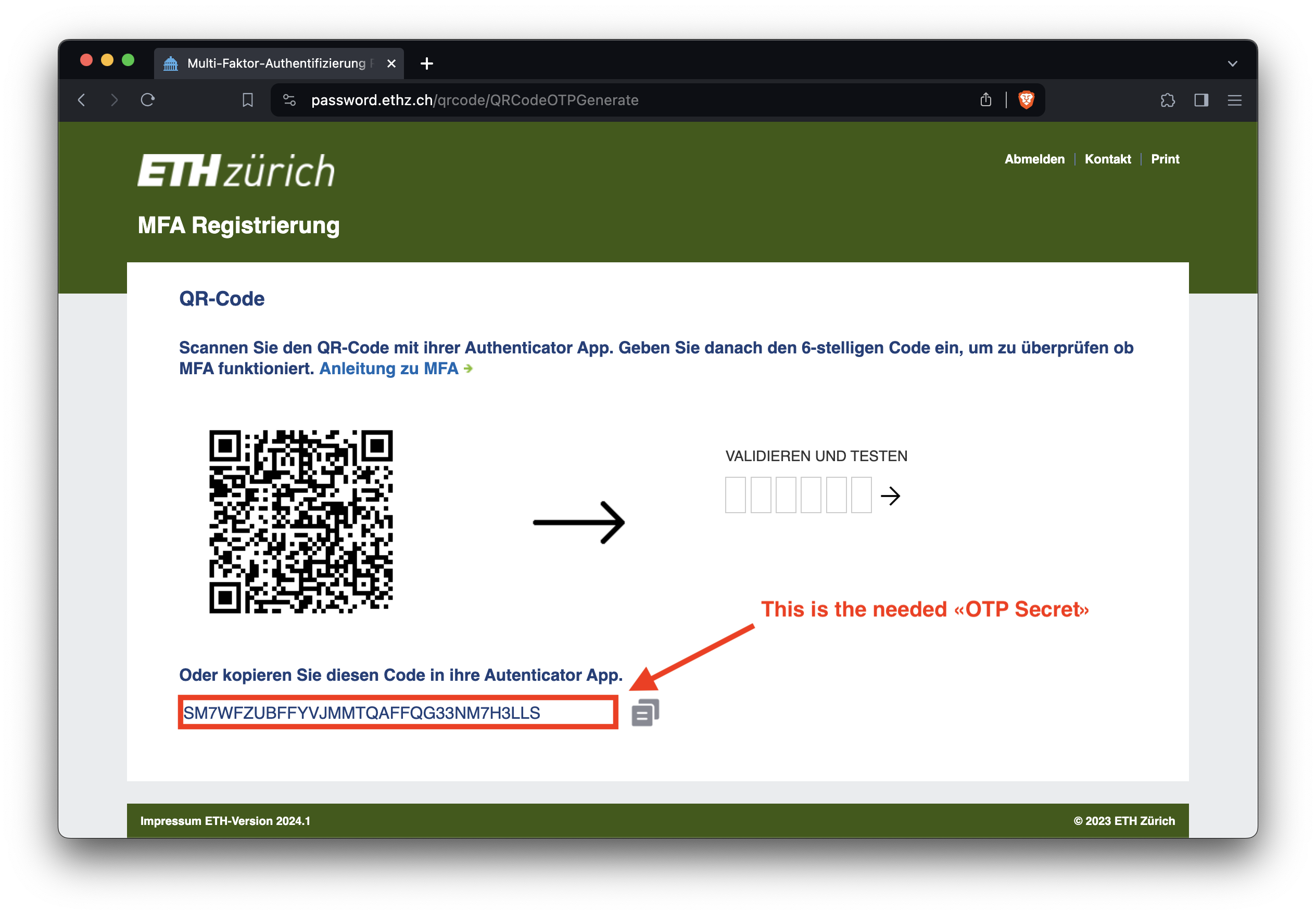
See also:
If you don't have the OTP Secret you can reset it and register again or – if you are using the Google Authenticator App – you can "get" the OTP Secret from there, but the procedure is quite complicated and not covered in this document (see for instance this project).
